Modern kids start using their smartphones at a pretty early age. By the age of 11, about 50% of children in the United States get their first device.
Younger kids use smartphones mostly to entertain themselves and do some silly things. Teens can also use phones for educational purposes and to stay in touch with friends on social media.
By the way, what OS does your child use? We bet most parents will say “Android,” as it has occupied the leading position among operating systems for mobile phones worldwide.
Table Of Contents
Is Android That Popular? Check Out the Statistics
Did you know that Google’s Android counts for around 1.6 billion users so far? More and more people buy Android-operated devices, and that number is only increasing.
Here’s what experts in the industry tell about Android:
- In 2017, Android accounted for more than 80% of all smartphone sales to end-users worldwide;
- Android has a 57% share of the tablet market in the first quarter of 2021;
- Android is predicted to account for about 86% of all smartphone shipments worldwide in 2023;
- The number of Android smartphone users in the U.S. is forecasted to reach over 130 million in 2022.
Is It Safe for Kids to Use Smartphones Without Parental Controls on Android?
Although smartphones give kids a number of possibilities for education, entertainment, and communication, unprotected Android-operated devices may pose a severe danger. It includes cyberbullying, online predators, and digital scammers.
Android phones are fragile in terms of online safety. For example, the overall number of new Android malware samples counted about 482,579 per month in March 2021. This means that thousands of Android users became victims of stealing identities and credit card details.
Bullies and predators don’t even have to hack someone’s mobile phone or run malware. All they need to do is create a free account on social media and befriend a kid.
It is a good reason for parents to learn how to set parental controls on Android. It’s such a relief to know that there are 3 possible ways to do it.
How to Set Parental Controls on Android: 3 Methods
1. Using a Parental Control App for Android
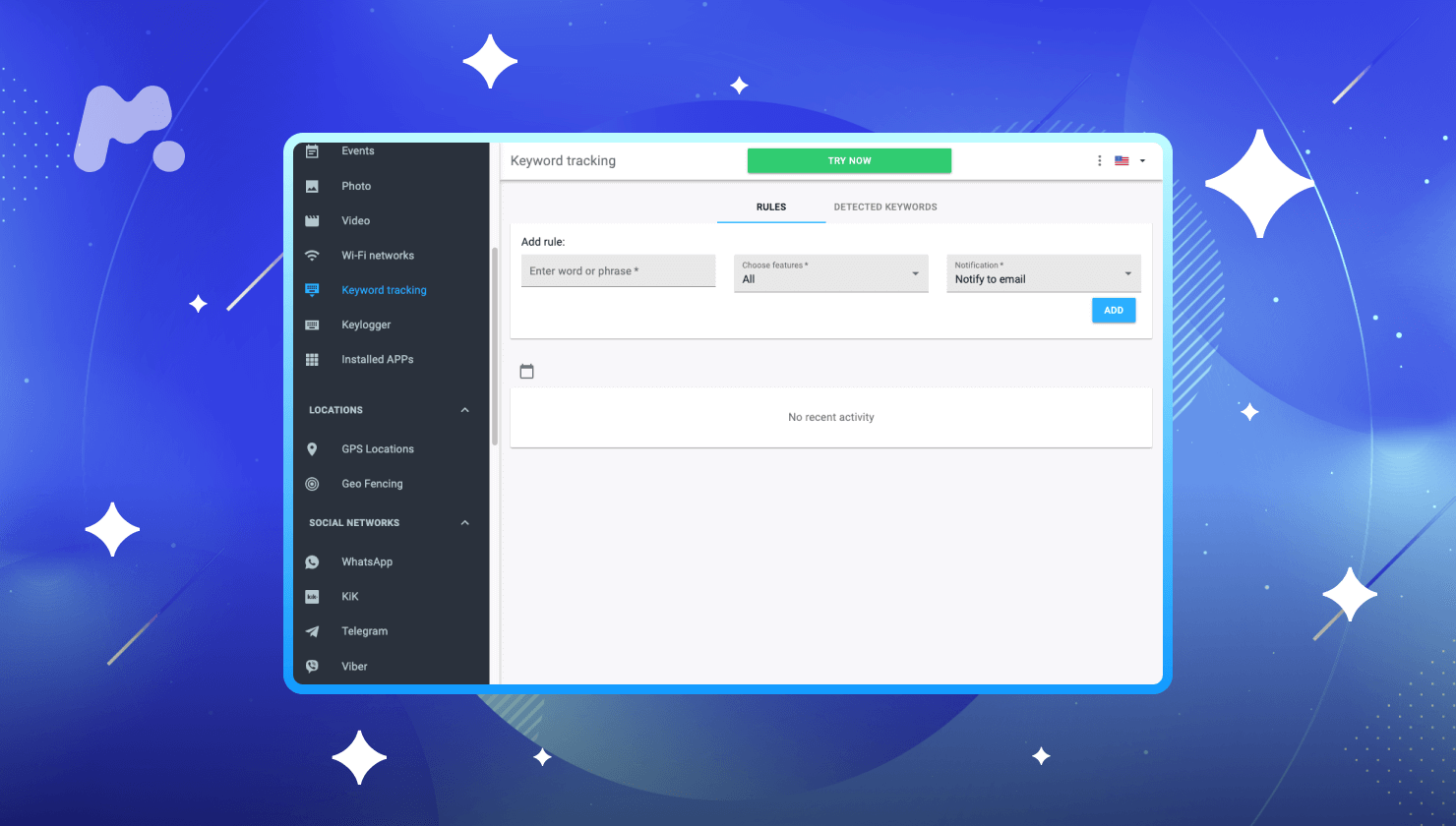
If you seek advanced parental controls for android cell phones, we have good news. A parental control app, such as mSpy, can come in handy for parents who need various parental features in one app.
With mSpy, you can monitor your kid’s online activity, record their keystrokes, and lock Play Store to prevent them from downloading age-inappropriate apps.
Follow these steps to set up mSpy on Android:
- Go to mspy.com and create an account.
- Purchase the subscription that suits your needs. Fill in the billing information, choose a payment method, and then submit your order.
- Use the installation instructions emailed to you after making a purchase and set up the app on your kid’s Android device.
- Log in to your mSpy dashboard and start monitoring your child’s online activity.
2. Setting the Android Kids Mode
Most devices have both main and sub-accounts, and Androids are no exception. As the main account owner, you can set secondary accounts for your kids.
To create Restricted accounts for your children, follow these steps:
- Go to the Settings menu on your child’s Android phone.
- Scroll down and tap Users.
- Click Add user or profile and select Restricted profile.
- Set up a password for the account if you haven’t done that before. Choose a PIN, pattern, or password.
- In the new screen that appears, find the list of all the installed apps with the ON/OFF buttons next to them.
- Name the profile.
- Select apps to enable your child’s profile. Tap the toggle buttons to the ON position.
- Exit Settings and lock the phone screen. Activate the screen by pressing the Home button. The lock screen shows usernames, and you can choose the needed name to unlock the screen using the PIN, pattern, or password you recently set.
3. Enabling Parental Controls in Play Store

If you are bothered with the question “How to block downloading apps on android?” there is a solution. You can enable parental settings right in Google Play Store:
- Open Google Play Store on your child’s Android phone.
- Head over to Settings.
- Under the User controls heading, find the Parental controls option and tap it.
- Parental controls are off by default. Turn them on.
- Enter a 4-digit PIN code. It will be used later to change settings for your parental controls. Confirm the PIN.
- Now, tap Apps & games.
- In the new window, choose age rates for apps. Tap the rating according to your child’s age and interests.
What Android Parental Control Is the Best for You?
If your kids are small and use your phone or tablet to play games, you can keep it simple and set a restricted profile on your device.
For older kids who know how to download and install apps, there is an option to enable parental controls in the Play Store. However, you need to note that they are likely to overcome the restrictions. There is no greater fun for children than violating rules, right?
So, if you seek a parental monitoring option that combines multiple functions, consider using mSpy.